“All models are wrong, but some are useful”, is an often repeated saying. Even though the Purdue model has been around for three decades and OT networks have moved beyond its hierarchical structure, it still deserves our consideration as a model that may help guide future work in this area.
Segmentation framework and DMZ requirement from the model continue to provide the basis for ensuring ICS security.
What is the Purdue Model?
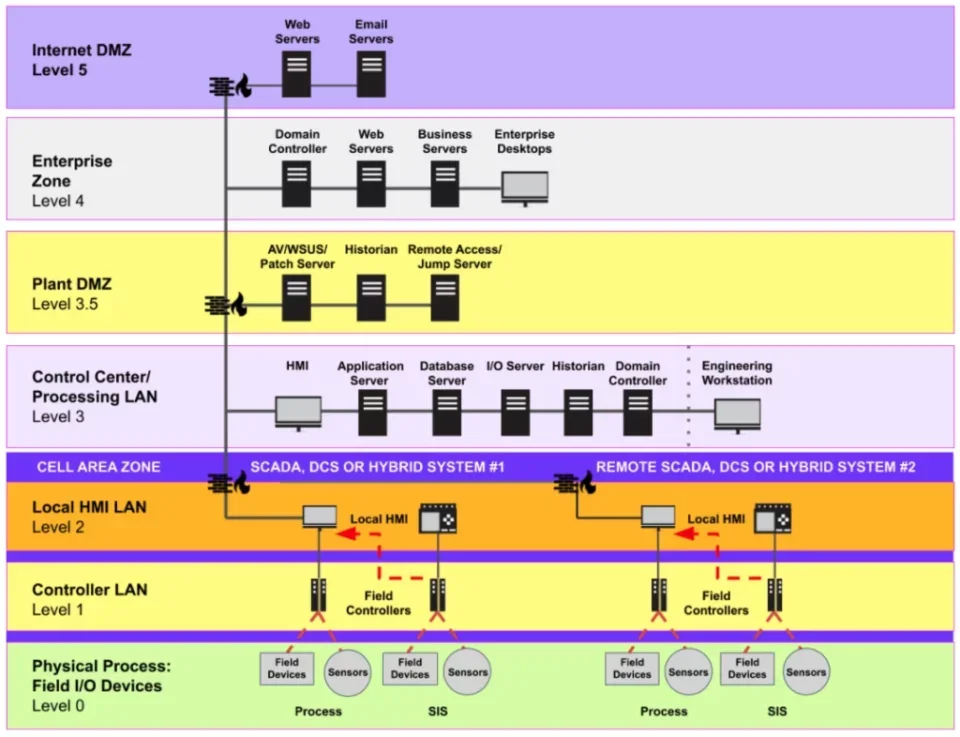
The Purdue Model has long been one of the cornerstones of industrial automation. First developed in the 1990s, its reference architecture provided a framework for how information technology (IT) and operational technology (OT) systems interconnect and communicate. Separating network elements into six zones, and outlining data flows between those levels. Implemented correctly, it creates an air gap between OT networks and IT networks to enable effective security controls.
This model divides operational technology (OT) and information technology (IT) components into six layers spanning from Level 0 through 5. Level 0 represents physical process components like sensors and IIoT devices; Level 1 represents basic control equipment like programmable logic controllers and other control equipment; Level 2 represents area supervisory control via human machine interfaces or supervisory control and data acquisition (SCADA) software; Level 3 represents site operations with centralised control terminals while level 4 addresses site business planning and logistics, wherein OT systems report upstream IT systems that collect and aggregate lower level data for management purposes. The level 5 is the main IT layer.
Though the Purdue model has served its purpose well, its application to today’s rapidly advancing technologies can no longer remain static. Sensors and actuators at Level 0 are gradually being given intelligence so they can transmit data directly into the cloud instead of going through other devices at higher levels of the hierarchy first. Furthermore, IT and OT boundaries cannot longer be clearly separated as per this model’s tenets.
Even with its limitations, the Purdue model remains relevant as an operational security framework. Indeed, cybersecurity discussions or presentations often incorporate reference to this model.
Purdue’s model offers an ideal framework for implementing security measures such as lateral movement protection and zero trust best practices at multiple layers. Implementation of such safeguards reduces vulnerability to cyber attacks significantly.
Purdue Model Definition
The Purdue model provides an information hierarchy for computer-integrated manufacturing (CIM) that helps secure industrial systems. It involves segmenting an OT network and controlling access to its components; with traditional models creating IT and OT zones separated with a DMZ to protect OT systems from unwanted IT traffic while permitting administrators to enforce security without disrupting operations.
As IoT allows more devices to access operational networks, maintaining a firm air gap between IT and OT systems becomes increasingly challenging. Many modern OT devices utilize cellular or other connections which allow direct communication with cloud monitoring software directly instead of going through Purdue Model’s Level 0. As a result, new potential points of exposure arise at Level 0 with intelligence being added into sensors and actuators – such as smart motors which monitor condition while making real-time adjustments on production line – creating additional potential points of exposure at Level 0.
At each level of an organization’s hierarchy, it is vital for ICS cybersecurity measures to be put in place at every layer – including network segmentation and remote access best practices. Furthermore, patching known vulnerabilities should include visibility into device connections as well as enforcement through lateral movement protection.
There are ways to bridge the gap between Purdue’s model and IIoT reality, however. Implementing Claroty’s Secure Remote Access (SRA) solution may help protect OT environments from cyber attacks by creating one encrypted tunnel for intra-facility communications and eliminating multiple remote access tools for each application. Users gain access according to roles and policies while the platform centrally manages user credentials and administrators can track all remote connection activity at any time.
As cyberattacks on OT networks continue to rise, manufacturers must implement strong OT cybersecurity. A network segmentation framework based on Purdue model can reduce attack risks while maintaining production throughput; to discover how your OT network can be secured securely contact us today.
Purdue Model Layers
The Purdue Model is a network segmentation framework that divides industrial control system (ICS) networks into six layers with different levels of control. This model is widely utilized across industries such as pharmaceuticals, oil & gas and food and beverage, automotive and more to improve ICS security by outlining components found within each layer and how data flows within them. OT professionals find this model especially helpful in understanding how best to secure their network infrastructure and identify vulnerable parts more quickly and protect them more easily.
Purdue’s model delineates physical processes involved in manufacturing products, with equipment like sensors and robots situated here. Centralized controllers for monitoring and controlling these processes reside here as well. Subsequent layers include site supervisory systems and operator terminals that manage operations of plants by collecting lower-level data and pushing it to an OT network for business decision making purposes.
Enterprise networks perform an array of IT duties, from data management and communication to reporting production status. This layer can include systems like ERP software, email servers and file servers – these often represent entryways into an OT environment for attackers so a secure network architecture is crucial in protecting these crown jewels from attack.
With cybersecurity threats ever evolving, it is critical that OT professionals keep informed on effective methods. While the Purdue model might not exactly fit an IIoT network’s cybersecurity strategy, starting here can help strengthen ICS security.
With technology’s continued advances, organizations are more frequently connecting their OT networks to the internet for cost and operational efficiencies. Unfortunately if not done by high skilled professionists, this opens them up to cyber attacks as hackers gain entry through this route; to combat this problem, Purdue model and NIST SP800-82/IEC 62443 standards place emphasis on segmenting the network into segments protected by logical network boundary controls that protect each one from attacks.
Purdue Model Security
The Purdue model is an established framework for designing and securing an Industrial Control System (ICS) network, placing emphasis on network segmentation to protect critical components of an ICS environment from attacks while restricting further threats’ spread through an ICS network. Furthermore, this model meets architecture requirements specified by industry standards such as NIST SP800-82, IEC 62443 and SANS ICS410 Reference Model.
While the Purdue Model remains an effective security solution for operational technology (OT), some experts question its ability to keep pace with modern advances. IoT connectivity blurs the line between IT and OT systems, no longer allowing OT systems to remain airgapped from enterprise networks; moreover, as sensors and actuators at Level 0 of the ICS hierarchy become smarter, this opens up new points of exposure not considered by Purdue model.
There are, fortunately, ways of adapting the Purdue model to new realities and meeting these concerns. For instance, operational technology teams should be engaged early in the design process when selecting new technologies so as to address security concerns from an early stage. This is really important and we suggest to contact us at the early stage of the projects.
An effective OT risk evaluation can also identify critical vulnerabilities to be prioritized for patching, as well as compensating controls like strong authentication and least privilege that can help fill any gaps and strengthen overall ICS security posture.
Purdue model should remain an integral component of modern ICS security strategies, but must also be combined with other elements to form an effective defense-in-depth to reduce attack risks. For example, using an identity-aware firewall to manage communication between switches and implementing strict macro segmentation to secure Level 0 and 1 devices are two tools which will provide optimal protection from known exploits as well as any malicious actors that gain entry at lower levels of an ICS architecture.