After IoT devices have been deployed into the world, it may be necessary to update them for additional security or functionality but gaining physical access to the device may no longer be possible or might be very costly. In 2015, Fiat Chrysler Automobiles, the world’s seventh largest automaker, issued a safety recall notice for 1.4 million vehicles in order fix a software hole that allowed hackers to wirelessly break into some vehicles and electronically control vital functions. Vehicle owners were left on their own to install the patch, which would typically be done by downloading the patch to a USB drive, then plugged into a vehicle port and uploading (source).
Fortunately today, there are over-the-air (OTA) software and firmware updates that allow embedded devices to be reprogrammed over their wireless connection instead of with a physical hardware device. In short, an OTA update is the wireless deployment of new software, firmware or other data to edge devices /Internet of Things use cases like consumer electronics, automobiles and smart sensors.
The Value Of OTA Updates
The value of OTA update capabilities within connected devices include a more convenient and cost efficient update process that reduces manual labor and saves time while allowing for remote updates for entire fleets. An OTA update allows for a quick response to security issues with new patches or changes in customer needs with new functionalities enabling companies to have fast innovation cycles and to stay competitive on the market. To minimize disruption to operations, OTA updates can be scheduled and geographically targeted to distributed fleets. Due to its significant business value, analysts forecast that the global market for over-the-air updates is expected to grow from 3.5 billion dollars in 2020 to over 10 billion dollars by 2027.
The Existing Challenges of OTA Updates
Nonetheless, a successful OTA update requires complex coordination between IoT hardware, device firmware, network connectivity, and traditionally, an IoT device cloud. There are geographical challenges to software updates for distributed device fleets, hardware complexity as different components require compatible software updates and updates to large device fleets are prone to error. Security and reliability are serious concerns during an OTA update as well. The solutions to these difficult challenges have their financial costs. As a result, the configuration of a secure and scalable OTA update is complicated, inconvenient and costly, taking away time and resources from IoT business and their development teams.
Introducing Husarnet Action For GitHub Actions: Direct OTA Deployment To Edge Devices
Husarnet is an open source P2P overlay network that is both a VPN and SDN type solution. Husarnet Client is installed directly on hardware devices that allows them to function as if they had a public IP even if they are hidden behind NAT or firewall. Read more about how Husarnet works here.
GitHub Actions is a popular Continuous Integration / Continuous Deployment (CI/CD) tool that allows developers to build workflows by using blocks automating common tasks called Actions. One of these automated GitHub Actions building blocks is now Husarnet Action!
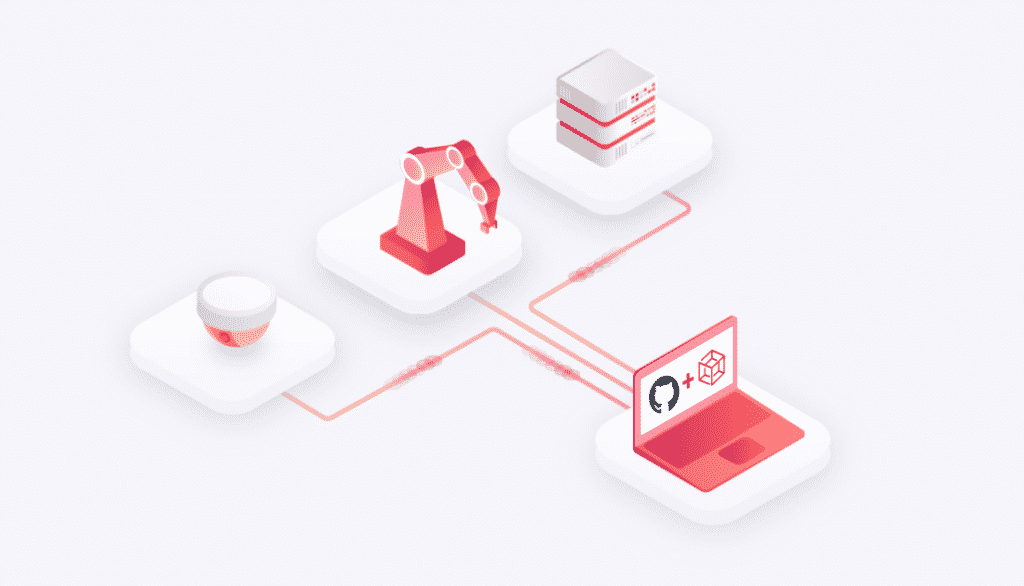
IoT developers can leverage Husarnet Action in their workflows to deploy code to hosts with no public or static IP addresses like laptops, Raspberry Pis, or even to ESP32 microcontrollers. With Husarnet Action allowing devices to act like they have a public IP address, it enables CI/CD pipelines to work not only for servers but also directly for IoT and edge devices.
This makes OTA updates much simpler and convenient because the automated Husarent Action allows firmware to be sent directly to an edge device without the need for complicated configuring with an intermediary IoT device cloud.
Find a free to use Husarnet Action in the GitHub marketplace: https://github.com/marketplace/actions/husarnet
Direct OTA vs OTA Server Approach
Let’s compare a traditional approach to OTA deployment with that powered by Husarnet (direct OTA)
| The traditional OTA (OTA server) | Husarnet powered OTA (direct OTA) |
|---|---|
| 1. A developer writes code and pushes it to a repository. | 1. A developer writes code and pushes it to a repository. |
| 2. A CI/CD workflow prepares new firmware. | 2. A CI/CD workflow prepares new firmware and sends it directly to the Edge/IoT device (OTA target). |
| 3. The new firmware is sent to an OTA server with a public IP address | |
| 4. An edge/IoT device (OTA target) is pinged: “Hey, there is a new firmware under this URL. Check it out.” | |
| 5. An Edge/IoT device attempts to download the new firmware from the given URL. |
Benefits of Direct OTA
The benefits of an OTA update powered by Husarnet Action include:
- Simpler architecture: there is no separate OTA server pinging the device to download a new firmware update from a URL. With Husarnet Action, firmware is directly uploaded to the device instead of asking to be downloaded from a given server.
- Easy and direct integration of OTA with popular CI/CD tool GitHub Actions.
- Standardization: the deployment to an Edge/IoT device now looks the same as a regular server.
- Security: Direct OTA means IoT developers can easily program each IoT/edge device with slightly different versions of firmware without exposing other firmware versions to other users: For example, let’s take a use case with 1000 devices where each device needs to have a new firmware with a unique private key that can not be exposed to other users. In a standard OTA system you would need to have a separate “server/sandbox” for serving just this specific firmware, for a given device, to prevent access to that device by other devices. With Husarnet Action, a specific firmware build is sent directly to a given device, without hosting that firmware under a public URL.
Direct OTA Deployment To A Fleet
Husarnet Action is an efficient over-the-internet solution for deploying firmware directly to IoT devices both for SBC (a Single Board Computer – like Raspberry Pi) and microcontroller (like ESP32). During prototyping and development, an OTA firmware update may be deployed to a single edge device. As larger numbers of devices are deployed, making the update process easy and secure is critical to business. It is essential for IoT companies to have the ability to safely execute OTA updates to many devices at one time to allow the roll out of new software features, fix bugs, or patch security issues across an entire fleet.
By combining GitHub Actions workflows powered by Husarnet Action with matrix of different job configurations, IoT developers can not only deploy their code to a single device but to the whole fleet at once without the need for an IoT cloud. The code and remote firmware update setup are covered by a version control in a single GitHub repository functioning as a true Infrastructure as Code way of handling IoT fleets.
Check the example how to configure matrix build with Husarnet Action in our latest tech blog post.
Just Add A Few Lines Of Code To GitHub Actions Workflow
Husarnet Action is a fast and convenient solution to automate the direct OTA deployment of code to edge devices at scale without the complexity of solutions used today. On the Husarnet technical blog, IoT developers can learn how to leverage Husarnet Action in a workflow to deploy code to devices with no public IP by adding just a few lines of code to your existing GitHub Actions yaml file.
For example the latest post features two GitHub repository templates allowing IoT developers to test Husarnet Action in practical use cases:
| Example project | Description |
|---|---|
| esp32-internet-ota | A template project with CI/CD for Over The Air (OTA) firmware update to ESP32 via the Internet, directly from GitHub workflow. Read more… |
| ga-rsync-demo | Showing how to copy files / build artifacts from GitHub workflow directly to Raspberry Pi (or other edge / IoT devices) with rsync. Read more… |
Visit the Husarnet Tech Blog for more information on Husarnet Action for GitHub Actions.